FAQ for CVE-2023-22524
General Information
A critical severity Remote Code Execution (RCE) vulnerability was discovered in the Atlassian Companion app (CVE-2023-22524).
This page contains answers to frequently asked questions about this vulnerability. The Atlassian Security Team will update this page whenever new information becomes available.
Is my Confluence instance affected?
This vulnerability affects the Atlassian Companion app on macOS only. The app is an optional desktop tool for Confluence Data Center and Server users. However, former app users, including those who may have recently migrated to Confluence Cloud, may still be vulnerable and should take care to remove it from their devices.
The Microsoft Windows version of the Atlassian Companion app is not affected by this vulnerability. It also does not affect Confluence Server, Confluence Data Center, or Confluence Cloud sites.
More details are available on CVE-2023-22524.
Are Cloud instances affected?
No, Atlassian Cloud Instances are not affected by CVE-2023-22524. If your Confluence site is accessed via an atlassian.net domain, it is hosted by Atlassian and is not exposed to this vulnerability. Additionally, the ability to edit content hosted on Confluence Cloud via the Atlassian Companion app was removed at the end of March 2022.
The Atlassian Companion app installed on Microsoft Windows is not affected. However, if an affected version of the Atlassian Companion app was installed on a macOS client machine in the past, and has not auto-updated to the latest app version, then the macOS client machine is vulnerable to CVE-2023-22524.
In such case, please either upgrade the Atlassian Companion app to version 2.0.0 or later, or uninstall the affected version of the app immediately from the macOS client machine.
Are other Atlassian products affected by this vulnerability?
No, they are not affected by CVE-2023-22524. Please make sure to check Security Advisories | Atlassian for other recent security advisories that might affect other Atlassian products you use.
Is my machine affected?
The Atlassian Companion app installed on Microsoft Windows is not vulnerable to CVE-2023-22524. This CVE affects versions of the Atlassian Companion app prior to v2.0.0 installed on macOS only.
How do I verify the Companion App version installed on my machine?
CVE-2023-22524 affects the Atlassian Companion app installed on macOS only. The Atlassian Companion app installed on Microsoft Windows is not affected.
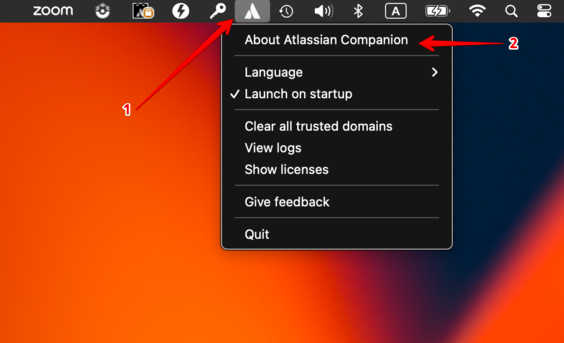
To confirm if the Atlassian Companion app is installed and running on a macOS client machine, please check the menu bar for the Atlassian Companion app icon:
Clicking About Atlassian Companion will show the app’s version:
The Atlassian Companion app must be version 2.0.0 or later (which has the fix for CVE-2023-22524).
If the macOS client machine is running an affected version of the Atlassian Companion app, please restart the app and ensure that the macOS client machine has an active internet connection to trigger the auto-update of the app.
If the macOS client machine can't connect to the internet, uninstall the Atlassian Companion app from that machine.
What is the impact of uninstalling Atlassian Companion app?
The Atlassian Companion app enables users to edit Confluence files in their preferred desktop application, and then save the file back to Confluence automatically.
The download and re-upload of files is managed by the Atlassian Companion app, which needs to be installed on each user's machine (not in the Confluence installation directory) to enable file editing.
Uninstalling the Atlassian Companion app from client machines will result in users being prompted to re-install the latest Atlassian Companion app the next time they press the Edit button on a Confluence attachment preview page.
How can I disable the Companion App from my instance?
No, it is not possible to disable the Atlassian Companion app through the Confluence Server or Data Center application to mitigate against CVE-2023-22524.
If the macOS client machine is running an affected version of the Atlassian Companion app, please restart the app and ensure that the macOS client machine has an active internet connection to trigger the auto-update of the app.
If your macOS client machine can't connect to the internet, uninstall the Atlassian Companion app from that machine.
Does patching to a fixed version solve the issue?
Yes. Version 2.0.0 or later of the Atlassian Companion app on macOS is not vulnerable to CVE-2023-22524.
I am running an affected version of Atlassian Companion app. How can I mitigate the threat until I patch it?
If the macOS client machine is running an affected version of the Atlassian Companion app, then please restart the app and ensure that the macOS client machine has an active internet connection to trigger the auto-update of the app.
If your macOS client machine can't connect to the internet, then uninstall the Atlassian Companion app from that machine.
Can we determine if the Companion app has already been compromised?
Atlassian does not have access to each customer’s end-user client machines and their communication (through the Atlassian Companion app) to the Confluence instance. Therefore, we cannot confirm if your instances have been affected by this vulnerability. You should engage your local security team to check all affected Confluence instances for evidence of compromise.
My macOS client machine has been compromised, what should I do?
The attack vector consists of utilizing WebSockets to bypass Atlassian Companion’s blocklist and macOS Gatekeeper to allow the execution of code.
We strongly recommend involving your local security team or engaging an external specialist security firm for further investigation of the compromised client machine.
I wasn't made aware of the vulnerability, how and when was this communicated by Atlassian?
An alert was sent out to all customers subscribed to the product technical alerts list after we had developed a fix. You can check your membership on that list by going to https://my.atlassian.com/email.
What if I don’t have a local security team?
We recommend engaging a specialist security firm for further investigation.