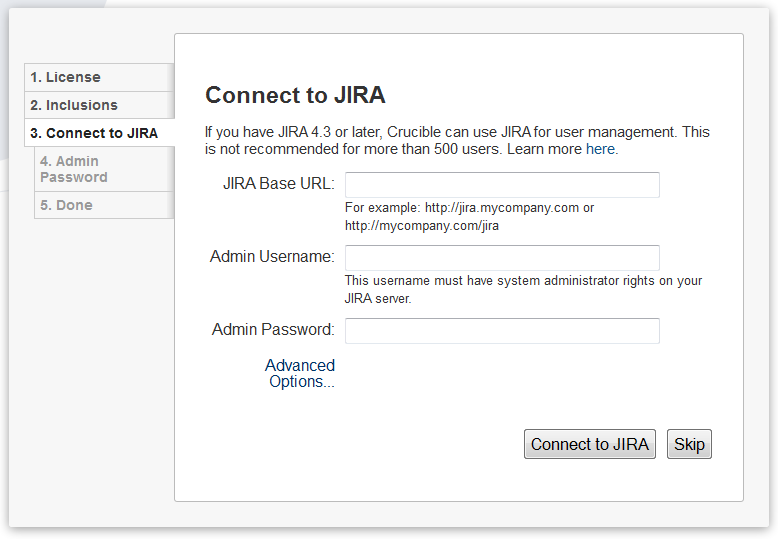
Configuring JIRA Integration in the Setup Wizard
This page describes the 'Connect to Jira' screen of the Crucible setup wizard.
You can also configure the JIRA connections via the application administration screens. In that case, you will need to set up connections individually. There are two parts to the integration process:
- A peer-to-peer link between JIRA and the application for sharing information and facilitating integration features. This link is set up via Application Links.
- A client-server link between the application and JIRA for delegating user and group management to your JIRA server.
Requirements: You need JIRA 4.3 or later.
On this page:
Connecting to Jira in the Setup Wizard
To configure Jira integration while running the Crucible setup wizard:
- Enter the following information on the 'Connect to Jira' step of the setup wizard:
Jira Base URL– The web address of your Jira server. Examples:
http://www.example.com:8080/jira/ http://jira.example.com- Admin Username and Admin Password – The credentials of a user with the 'Jira System Administrators' global permission in Jira.
- Fisheye/Crucible Base URL – Click 'Advanced Options' to see this field. Jira will use this URL to access your Fisheye/Crucible server. The URL you give here will override the base URL specified in your Fisheye/Crucible administration console, for the purposes of the Jira connection.
- Groups to synchronize – Click 'Advanced Options' to see this field. Select at least one Jira group to synchronize. The default group is
jira-users. Jira will synchronize all changes in the user information on a regular basis. The default synchronization interval is 1 hour. - Admin Groups – Click 'Advanced Options' to see this field. Specify a Jira group whose members should have administrative access to Fisheye/Crucible. The default group is
jira-administrators.
- Click the 'Connect to Jira' button.
- Finish the setup process.
- Configure the following setting in Jira: Allow remote API access.
Screenshot: Connecting to Jira in the Fisheye/Crucible setup wizard
Troubleshooting
Notes
When you connect to Jira in the setup wizard, the setup procedure will configure Trusted Applications authentication for your application. Please be aware of the following security implications:
- Trusted applications are a potential security risk. When you configure Trusted Applications authentication, you are allowing one application to access another as any user. This allows all of the built-in security measures to be bypassed. Do not configure a trusted application unless you know that all code in the application you are trusting will behave itself at all times, and you are sure that the application will maintain the security of its private key.